Vulnerability Scanning
Detect CVEs with NVD and CISA KEV integration.
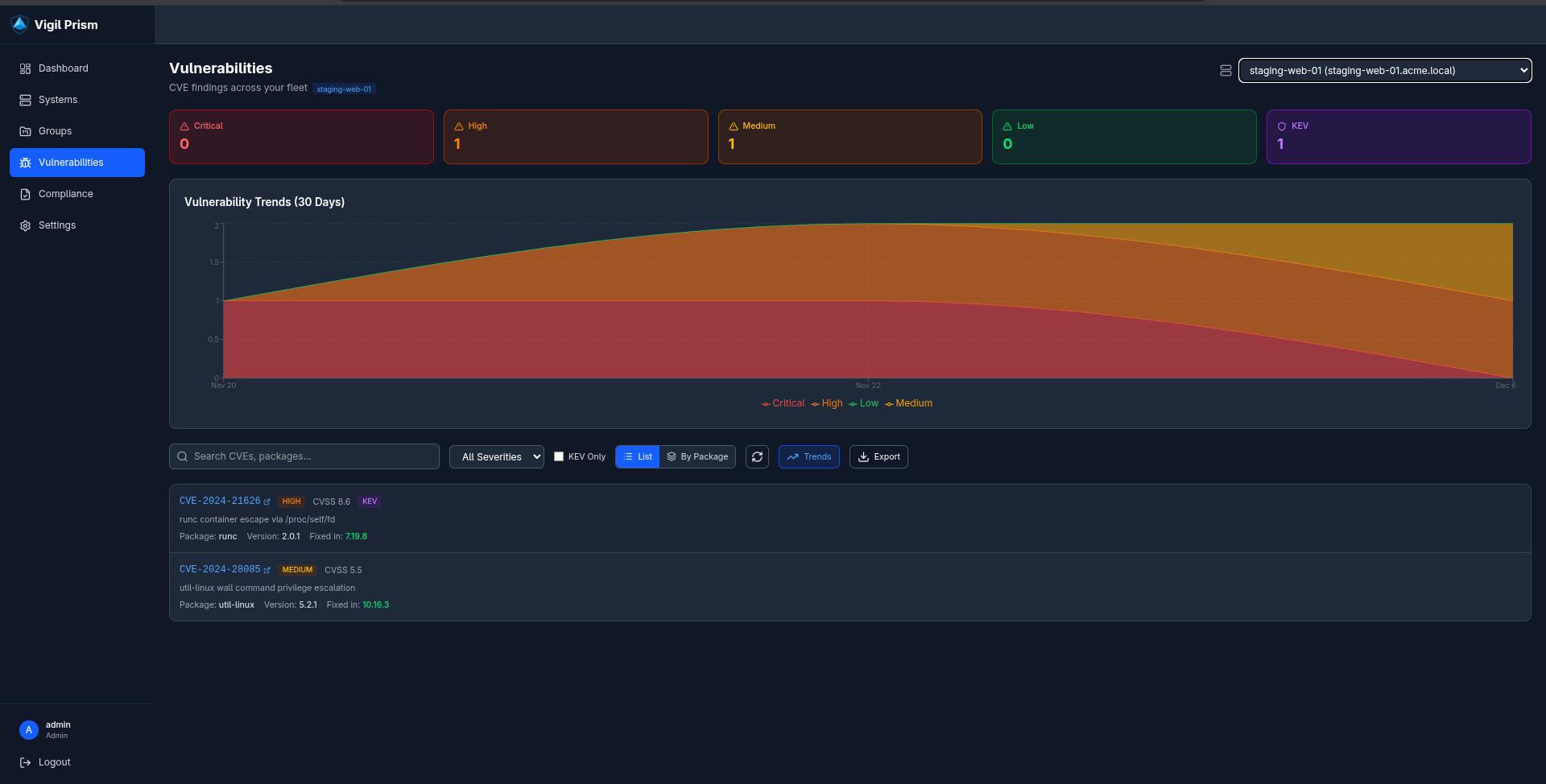
The Vulnerabilities page showing CVE findings with severity trends(click to enlarge)
How It Works
VigilPrism scans installed software and compares versions against known vulnerabilities:
- 1Software Inventory - Agent catalogs installed packages and applications
- 2CVE Matching - Versions compared against NVD database
- 3KEV Enrichment - Known exploited vulnerabilities flagged as critical
- 4Prioritization - Results sorted by severity and exploitability
Data Sources
NVD (NIST)
National Vulnerability Database - comprehensive CVE data with CVSS scores
CISA KEV
Known Exploited Vulnerabilities - actively exploited in the wild
Understanding CVSS Scores
| Score | Severity | Recommended Action |
|---|---|---|
| 9.0-10.0 | Critical | Patch immediately |
| 7.0-8.9 | High | Patch within 1 week |
| 4.0-6.9 | Medium | Patch within 30 days |
| 0.1-3.9 | Low | Schedule for maintenance |
CISA KEV Vulnerabilities
Vulnerabilities in CISA's Known Exploited Vulnerabilities catalog are being actively exploited by attackers.
These should be patched immediately, regardless of CVSS score.
Running Vulnerability Scans
Via Dashboard
Navigate to Systems → select agent → Run Vulnerability Scan
Via CLI
sudo vigilprism-agent --vuln-scan
Via API
curl -X POST http://server:8000/api/v1/systems/{agent_id}/audit \-H "Authorization: Bearer $TOKEN" \
-d '{"include_vulnerability_scan": true}'Example Vulnerability Finding
{
"cve_id": "CVE-2024-1234",
"package": "openssl",
"installed_version": "1.1.1k",
"fixed_version": "1.1.1l",
"cvss_score": 9.8,
"severity": "critical",
"in_kev": true,
"description": "Buffer overflow vulnerability...",
"remediation": "apt update && apt upgrade openssl"
}